Table of contents
The clock is ticking, MIM's end-of-life is just three years away. Many organizations realize a new identity solution is inevitable. But this necessary transition is not just about avoiding future risk, it's also a massive opportunity. Your move from MIM is a chance to modernize identity operations for productivity, agility, and compliance.
We've covered the risks of staying put. Now, we'll focus on the essential strategy: how to handle the move safely, make it efficient for your business in the long term, and preserve (or even raise) your security and compliance posture when shifting to a modern identity platform.
Understanding what needs to be recreated when leaving MIM
Moving off MIM is like rebuilding a historical, heavily customised vault and migrating its contents (in this case, identity data) to a modern security facility.
The transition can be precarious – you must ensure every access review and audit trail is perfectly mapped to the new system, and that the new facility is configured correctly.
As I explain below, the configuration doesn’t simply mean you're moving a MIM-based mechanism into the new solution. It should allow you to apply modern protection features (like Zero Trust and Multi-Factor Authentication) that the old one couldn't support.
The success hinges entirely on meticulous pre-migration planning and treating security as the primary architectural blueprint, not an afterthought.
While many people call the transition away from Microsoft Identity Manager a “migration”, it is a broader project, i.e., a profound IAM modernization effort.
The core challenge lies in mapping MIM's functionality to a new, often cloud-based, environment. There are a few pillars that define MIM's role and must be rebuilt in any Microsoft Identity Manager replacement.
First, we must address the fundamental identity mechanics. Every connection, every logic step, and every flow that MIM handles should be properly recreated.
In my experience, the hardest part of this transition is not the “obvious” configuration pieces. I believe that provisioning workflows are relatively easy to review and analyze in the MIM console.
The most difficult aspects are the things no one knows about. MIM environments often have numerous surrounding scripts. This external custom code is the most challenging element because its function is frequently unknown. Often, people simply do not realize it exists outside the MIM boundaries. Furthermore, auxiliary databases often contain complex, bespoke logic, performing calculations that feed back into the identity system.
Finding and dissecting this surrounding logic is critical to avoiding post-migration failure.
Custom code in MIM, frequently implemented as extensions, cannot simply be moved to a new platform. The reason why it’s so common is that it helped replace missing features or integrations. Custom-written code in MIM is typically configured through built-in provisioning rules or lifecycle flows in modern tools. We must analyze what it does and integrate that logic into the new environment's standard processes.
I recall a specific client case where the identity solution, Omada, could not accurately calculate a unique username and email for users.
We developed a workaround, which involved a small application running in Azure that received a notification on a new user. It would then query the directory (Entra), calculate the unique attributes based on defined rules, check for uniqueness, and finally update the identity in Omada to allow the account creation.
Sometimes, a workaround like this is necessary. But it requires deep-dive sessions with the client to understand precisely how they need the process to function, not just how it functions now. The old MIM setup simply serves as a reference to observe the current behavior, but the new design must align with the desired target state.
As opposed to what many businesses believe, a secure Microsoft Identity Manager replacement doesn’t start with tooling. Security and compliance must be your priority that should shape the platform choice from the first design discussion.
I never treat them as migration checkpoints to validate at the end. Once you slip into that mindset the damage is already done.
Continuity breaks most often during analysis. I've seen migrations fail over small details that got skipped. Someone defines a condition for the happy path, but nobody asks what happens when that condition isn't met. The workflow just stops without any fallback logic or audit trail. In a diagram, that gap looks harmless, but in production, it becomes a compliance issue.
Another common problem is misalignment between vendor and customer. A mechanism gets described and each side interprets it differently although both assume they're on the same page. Then the system behaves in ways nobody expected. Access reviews stop reflecting reality and certifications lose their meaning.
Maintaining continuity during migration means preserving how decisions are made, and how they're proven after the fact. This applies directly to access recertification and approvals that previously lived in Microsoft Identity Manager.
Here are a few key focus areas to maintain continuity:
When you run systems in parallel, the evidence trail gets split. Part of the data still lives in your old MIM database, and the rest is on the new platform. Auditors don't care about your migration plan; they only care if they can see the complete, end-to-end trail.
I’ve been through audits where teams had to spend hours explaining why approvals were handled across different systems. The process became slow and heavy. This wasn't because the security controls were weak, but because they were scattered and fragmented.
Cloud IAM platforms add another headache. Yes, you get logs – lots of them. But who owns them? Ownership is often unclear. Someone needs to be tasked with collecting those logs, while someone else must be responsible for actually reading them. Without that clear accountability, identity governance stops being a useful control mechanism and just becomes a massive data dump.
Security gaps rarely show up as a sudden, dramatic failure. They appear as a subtle "permission drift."
Keeping your Role-Based Access Control (RBAC) and Separation of Duties rules intact requires serious discipline and non-stop validation. When the stakes are high, I always rely on phased cutovers and parallel operation periods. This strategy is critical because it:
We need to stop seeing cloud directories as direct replacements for complex MIM systems. Even if an organization adopts a powerful tool like Entra ID, the level of governance depth it offers may not match what they enforced before. This is why supplemental Identity Governance and Administration (IGA) tools are often needed to close that gap.
I have seen this approach work wonders; it can patch governance holes very quickly.
However, I have also seen the downside where it can complicate audits. When controls span multiple systems, teams suddenly have to review access in two different places. If part of the work still runs through the legacy platform, the governance process becomes more demanding rather than the simpler solution everyone hoped for.
Segregation of Duties (SoD) exists for one reason: to prevent conflicting access that leads to abuse or costly errors. Conceptually, these rules are simple but operationally, they are dangerously easy to weaken during a migration.
When an IAM modernization project begins, I insist that all SoD rules are written down in operational terms:
These foundational rules must survive the move intact. If they fail even once during the migration, they will fail again later, I assure you. Preserving these rules is the ultimate test of whether your new platform deserves your trust.
When a client operates in a regulated industry, I always start by assessing their cloud maturity level rather than defaulting to on-premises.
Some regulated organizations are simply not cloud-ready. They might lack the necessary security framework, or they fear their sensitive data residing in a remote location. Others have addressed these concerns and are prepared to adopt cloud services under strict terms, often requiring specific data residency guarantees or dedicated environments. The decision is entirely determined by the organization's current stage of readiness.
Here, I want to underline that cloud solutions present an inherent trade-off – they are less customizable. We must accept the functionality available out-of-the-box and configure within those boundaries.
On the other hand, on-premises solutions, while offering the flexibility of custom code, introduce the perpetual challenge of verifying and adapting that code every time the vendor releases a new version or update.
When you move your identity services out of an on-premises system and into the cloud, you have to confirm that the service you've picked meets all the laws about where your sensitive data needs to live.
For this, you must understand the shared responsibility model. The cloud provider handles the security of the underlying foundation, i.e., the infrastructure. However, you, the cloud provider’s customer, are fully responsible for how you set up your identity policies and for watching out for any misuse. Getting the configuration wrong is a very common security mistake during migration, and it happens all the time.
I agree with Omada that, if your team doesn't grasp good security practices within a cloud environment, you essentially make it easier for attackers to mess with your cloud-hosted Identity Governance and Administration (IGA). Cloud environments are incredibly interconnected, which often lets traffic bypass the firewalls and defenses you used to rely on.
For regulated industries, like finance or any company dealing with strict GDPR data, keeping tight controls is mandatory. Imagine a bank moving off MIM; they need meticulous, upfront planning to satisfy standards like SOX and GDPR. This starts with building compliance into the migration plan from the very first day.
Moving away from MIM should never be about chasing new features for their own sake. It should focus on gaining visibility and control that your previous legacy platform simply couldn’t offer.
I don't view the absence of modern features in MIM as an automatic security disaster; organizations survived for years without them. The real difference is awareness. Older systems executed processes, but they rarely showed you what was really happening with access across your entire environment.
This is where modern identity platforms change the conversation. Zero Trust is no longer just a diagram on a slide. The core assumption changes: every access request is treated as suspicious until proven otherwise.
That assumption alone forces better discipline across the board. Multi-Factor Authentication (MFA) and Single Sign-On (SSO) stop being optional improvements and become the absolute default for every interaction.
However, the biggest shift I have seen comes from identity analytics. This is where identity governance moves from theory to real-world practice. Traditional MIM workflows granted access and then moved on. They never monitored the state of those permissions afterward. Modern IGA platforms do.
I remember seeing a compliance workbench view from Omada for the first time (you can see it below):
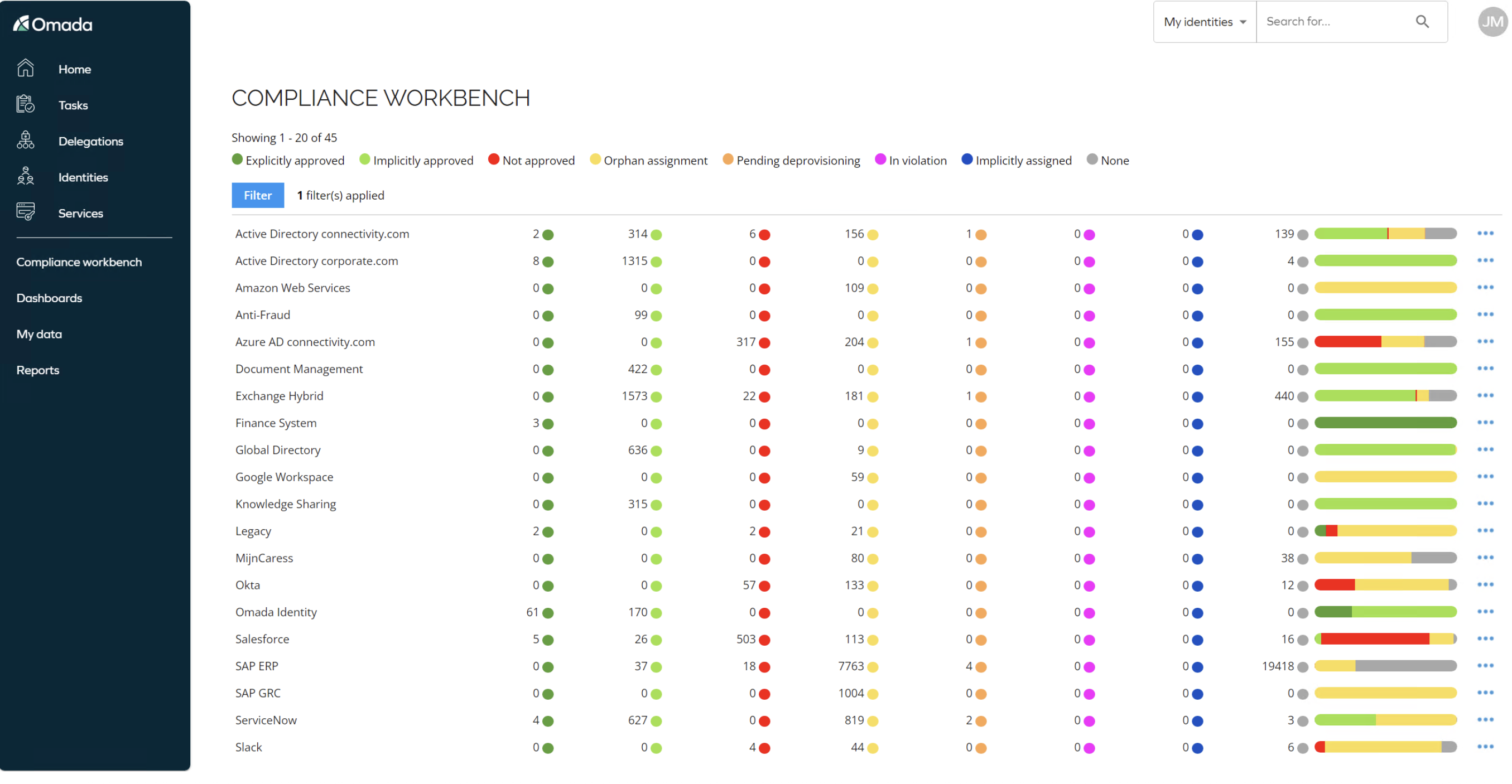
Most eye-opening were the permissions flagged as not approved. These were access rights that nobody, not even the system owner, could justify.
This kind of report opens your eyes immediately. You suddenly see hundreds of entitlements in systems like Salesforce that shouldn't exist. This usually isn't malicious; it's because access accumulates over time, and nobody ever cleans it up.
From here, the path is clear:
Once confirmed, the system remembers that decision. This finally breaks the cycle of forgotten access that quietly increases risk year after year.
MIM never did this, but a modern Microsoft Identity Manager replacement can. Not just because it's newer, but because it treats access as something that must be observed continuously rather than granted once and forgotten.
The move away from MIM is a specialized undertaking. While training internal teams or hiring new staff is an option, that path is often prohibitively costly and time-consuming.
In my experience, I rarely see organizations try to manage the migration build itself using only internal resources. They almost always engage professional services firms to implement the new solution. However, they frequently underestimate the weight of the pre-project analysis and the importance of selecting the right solution.
They might review vendor materials, run a quick proof of concept, and click through a few features. They see that the tool has certain features and think, "Okay, this will work."
But if you don't execute an upfront analysis properly, no matter how good the vendor is, the project will not deliver optimal results.
This is something you can address by working with an external identity expert. Among others, you:
Gain immediate expertise: you work with people who bring years of focused experience in the identity and data security domain and know the best practices for MIM replacement.
Lessen the decision pressure: the consultants take on the responsibility of deciding on the optimal technical solutions. Especially since your team lacks sufficient, hands-on experience with the new, modern platform.
Get dedicated focus: partnering means you have a team fully focused on the project execution. This allows your internal team to maintain concentration on your core services and business operations, ensuring minimum disruption and a higher quality implementation.
The move away from legacy Identity Management (MIM) is inevitable. With proper planning, this transition can happen without impacting business operations or compromising security.
However, organizations delaying the move face escalating risks. Legacy systems were not built for today's Zero Trust environment, leading to subtle security gaps like permission drift. Crucially, any delay will force compressed timelines later, resulting in control fragmentation and poor long-term choices under pressure.
A modern identity platform offers more than features; it provides the visibility and continuous control MIM never could. This shift to Identity Analytics turns governance into a continuous process which is the only way to audit permissions accurately and break the cycle of forgotten access.
QWEY offers comprehensive solutions for a controlled transition:
Immediate stability.
Our MIM Care service stabilizes and secures your current legacy environment, buying you critical time.
Strategic modernization.
We advise and implement modern, control-driven platforms, using Microsoft Entra ID, Omada Identity, and Azure cloud infrastructure.
Stop waiting for the clock to run out. Let QWEY guide your move and take back control.